Post-Quantum Cryptography: A Critical Safeguard for Cybersecurity in the Quantum Computing Era
Introduction
As quantum computing makes headway, conventional cryptographic algorithms face the imminent threat of obsolescence. Post-quantum cryptography (PQC) emerges as a vital solution to address this vulnerability, ensuring the protection of sensitive data and communication in the face of quantum computing advancements.
Understanding Quantum Computing and Its Impact on Cryptography
Quantum computers harness the principles of quantum mechanics to perform calculations that are exponentially faster than classical computers. This accelerated computational power poses a significant threat to current cryptographic algorithms, which rely on the difficulty of factoring large numbers and solving discrete logarithm problems. Quantum algorithms can potentially break these encryption mechanisms, jeopardizing sensitive data.
Post-Quantum Cryptography: A Protective Shield
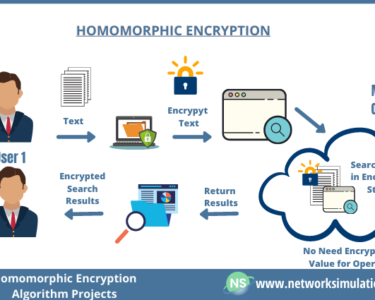
PQC encompasses cryptographic algorithms that are specifically designed to resist attacks by quantum computers. By adopting algorithms based on different mathematical principles, such as lattice reduction or multivariate polynomials, PQC safeguards sensitive information from potential quantum computing threats.
Advantages of Post-Quantum Cryptography
- Quantum Resistance: PQC algorithms are quantum-resistant, meaning they remain secure even against the most powerful quantum computers.
- Long-Term Security: PQC algorithms are designed to provide long-term protection against quantum computing advancements.
- Compatibility: PQC algorithms are interoperable with existing cryptographic systems, facilitating a smooth transition to quantum-safe cryptography.
Applications of Post-Quantum Cryptography
PQC finds applications in a wide array of sectors:
- Financial Transactions: Securing online banking, digital payments, and financial data.
- Government and Military: Protecting sensitive information related to national security and military operations.
- Healthcare: Safeguarding patient records, medical devices, and healthcare systems.
- Critical Infrastructure: Defending against cyberattacks on power grids, water distribution systems, and other vital infrastructures.
Implementation and Adoption
The standardization process for PQC algorithms is ongoing, with multiple candidate algorithms undergoing evaluation by international organizations. Governments, businesses, and individuals are urged to begin implementing PQC algorithms to ensure future cryptographic resilience.
Conclusion
Post-quantum cryptography is a crucial measure to safeguard cybersecurity in the face of quantum computing advancements. By adopting PQC algorithms, organizations can protect sensitive data, maintain communication integrity, and ensure long-term cryptographic resilience. As quantum computing evolves, PQC will become an indispensable tool for securing the digital landscape and safeguarding the future of cybersecurity.