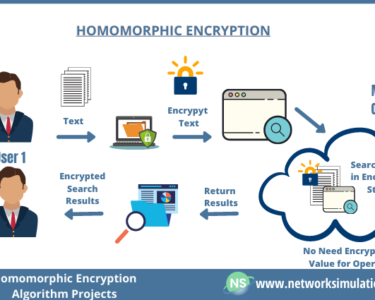
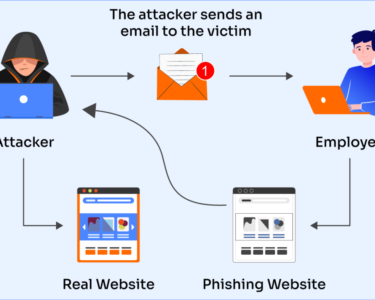
Guarding Against Insider Threats
Insider threats are a significant security risk for organizations of all sizes. They can come from employees, contractors, or other trusted individuals who have access to sensitive information and systems. Insider threats can be intentional or unintentional, and they can cause significant damage to an organization’s reputation, finances, and operations.
There are a number of steps that organizations can take to guard against insider threats, including:
- Implementing strong security controls. This includes implementing measures such as access control, encryption, and intrusion detection systems.
- Educating employees about insider threats. Employees need to be aware of the risks of insider threats and how to protect themselves and their organization.
- Monitoring employee activity. This can be done through a variety of methods, such as reviewing logs, tracking user behavior, and conducting security audits.
- Investigating suspicious activity. If an organization suspects that an insider threat may be occurring, it should investigate the matter thoroughly.
- Responding to insider threats. If an insider threat is confirmed, the organization should take appropriate action to mitigate the damage and prevent future incidents.
Insider threats are a serious threat to organizations, but they can be managed through a combination of security controls, education, monitoring, and investigation. By taking these steps, organizations can help to protect themselves from the risks of insider threats.
Additional tips for guarding against insider threats:
- Be aware of the signs of insider threats. These can include changes in employee behavior, such as increased access to sensitive information or attempts to bypass security controls.
- Report any suspicious activity to your supervisor or security team. It is important to report any activity that you believe may be a security risk.
- Follow security best practices. This includes using strong passwords, avoiding clicking on suspicious links, and being careful about what information you share online.
- Be vigilant. Insider threats can occur at any time, so it is important to be vigilant and aware of the risks.
By following these tips, you can help to protect your organization from the risks of insider threats.