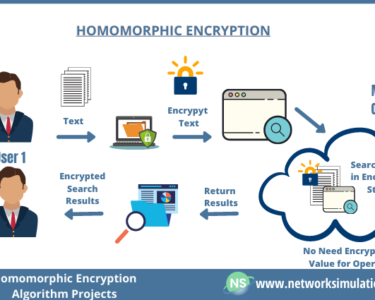
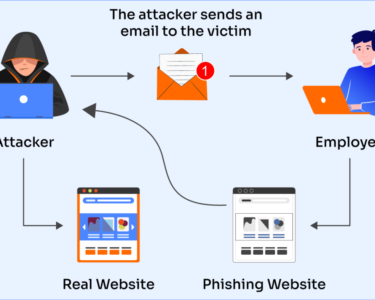
The Future of Authentication: Digital Security in the Face of Cyber Espionage
In the ever-evolving digital landscape, the safeguarding of sensitive information has become paramount. As cyber threats continue to proliferate, traditional authentication methods are proving increasingly inadequate. The future of digital security lies in the adoption of advanced authentication techniques that can effectively combat the growing threat of cyber espionage.
The Rise of Cyber Espionage
Cyber espionage, the unauthorized acquisition of confidential information through electronic means, has become a pervasive threat. State-sponsored and criminal organizations alike are employing sophisticated methods to infiltrate networks and steal sensitive data. These attacks can have devastating consequences for businesses, governments, and individuals alike.
The Limitations of Traditional Authentication
Traditional authentication methods, such as passwords and two-factor authentication (2FA), are no longer sufficient to protect against the ingenuity of cyber attackers. Passwords are easily hacked, and 2FA can be bypassed with the use of sophisticated malware.
Advanced Authentication Techniques
The future of authentication lies in the adoption of more advanced techniques that provide a higher level of security. These include:
- Biometrics: Biometric authentication uses unique physical or behavioral characteristics, such as fingerprints, facial recognition, or voice patterns, to verify a user’s identity. These methods are highly resistant to compromise.
- Multi-Factor Authentication (MFA): MFA combines multiple authentication methods, such as passwords, biometrics, and OTPs (one-time passwords), to create a layered defense. This makes it much harder for attackers to gain unauthorized access.
- Adaptive Authentication: Adaptive authentication dynamically adjusts the authentication requirements based on factors such as user behavior, location, and device type. This approach provides a flexible and context-aware security system.
- Zero Trust Authentication: Zero trust authentication assumes that all users are potential threats and verifies every request for access. This approach eliminates the concept of implicit trust and provides a comprehensive defense against cyber espionage.
Implementation and Challenges
The adoption of advanced authentication techniques requires careful planning and implementation. Organizations need to consider factors such as cost, user experience, and the integration with existing systems. Additionally, the deployment of these technologies can introduce new challenges, such as increased complexity and the need for specialized knowledge.
Conclusion
The future of digital security depends on the adoption of advanced authentication techniques that can effectively combat the growing threat of cyber espionage. By leveraging biometrics, MFA, adaptive authentication, and zero trust principles, organizations can create a robust defense that protects sensitive information from unauthorized access. While implementation may pose challenges, the benefits of enhanced security far outweigh the risks, ensuring the resilience of digital infrastructure in the face of evolving cyber threats.