Securing Cloud Services in the Digital Age
In the rapidly evolving digital landscape, cloud services have become an indispensable part of modern business operations. They offer a wealth of benefits, including scalability, cost-effectiveness, and global reach. However, the increased adoption of cloud computing also brings with it a heightened risk of cyber threats.
To protect sensitive data and maintain operational integrity, organizations must prioritize the security of their cloud services. Here are five key strategies to enhance cloud security in the digital age:
1. Implement Strong Access Controls:
Implement robust authentication mechanisms such as two-factor authentication (2FA) to prevent unauthorized access to cloud environments. Establish role-based access control (RBAC) to limit privileges and segregate duties. Ensure that least privilege principles are followed to minimize the impact of potential breaches.
2. Encrypt Data at Rest and in Transit:
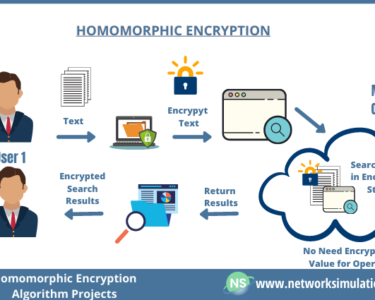
Encrypt sensitive data using strong encryption algorithms at both rest (stored in the cloud) and in transit (transmitted over networks). Encryption protects data from unauthorized access, even if it is intercepted or stolen.
3. Monitor and Audit Cloud Activity:
Continuously monitor cloud activity for suspicious behavior or anomalies. Establish audit trails to track user actions and identify any suspicious patterns. Regular security audits help identify vulnerabilities and ensure compliance with best practices.
4. Leverage Cloud-Native Security Services:
Take advantage of cloud-native security services provided by cloud providers. These services offer advanced protection features such as intrusion detection systems (IDS), threat intelligence, and automated security patching.
5. Foster a Culture of Security:
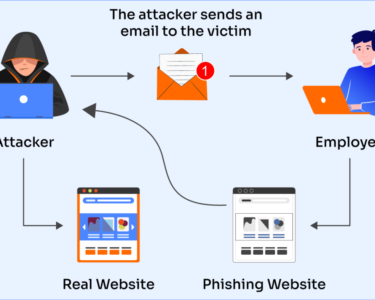
Create a culture of security awareness throughout the organization. Educate employees on best practices for cloud security, including proper password management and reporting suspicious activity. Foster a collaborative environment where individuals feel empowered to contribute to overall security.
By adhering to these strategies, organizations can significantly enhance the security of their cloud services and mitigate the risks associated with the adoption of cloud computing. It is crucial to remember that cloud security is an ongoing process that requires constant monitoring, evaluation, and adaptation to the evolving threat landscape. By embracing a proactive and comprehensive approach to cloud security, organizations can harness the benefits of cloud computing while safeguarding their data and maintaining operational resilience in the digital age.