Digital Security: Economics and Strategies
Introduction
In the digital age, ensuring the security of sensitive information has become paramount. The proliferation of digital devices, interconnected networks, and vast amounts of data has created a complex and challenging landscape for organizations and individuals alike. Digital security encompasses a wide range of measures and strategies aimed at protecting against unauthorized access, use, disclosure, disruption, modification, or destruction of digital information.
Economics of Digital Security
Digital security is not without its economic implications. Organizations and governments invest significant resources in implementing security measures, from hardware and software to personnel and training. These investments can be substantial, especially for critical infrastructure or organizations handling sensitive data.
The economic impact of digital security breaches can be severe. Data breaches can lead to loss of revenue, damage to reputation, legal liability, and other financial consequences. A study by the Ponemon Institute found that the average cost of a data breach in 2020 was $3.86 million.
Strategies for Enhancing Digital Security
To effectively protect against digital threats, organizations and individuals must adopt comprehensive security strategies. These strategies typically involve a combination of technical, administrative, and physical measures:
1. Technical Measures:
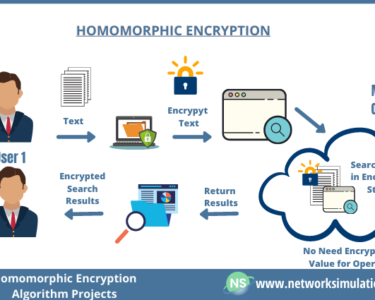
- Encryption: Encrypting data at rest and in transit prevents unauthorized access and disclosure.
- Network Security: Firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) monitor network traffic for malicious activity.
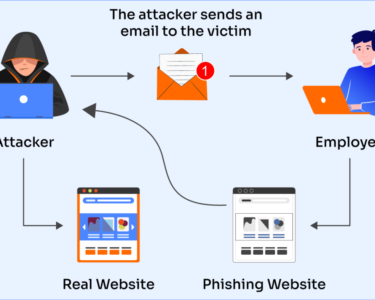
- Malware Protection: Anti-virus and anti-malware software detect and remove malicious software.
- Identity and Access Management (IAM): Systems that manage user identities, access rights, and authentication processes.
2. Administrative Measures:
- Security Policies: Establish clear guidelines for acceptable use of digital resources and security protocols.
- Training and Awareness: Educate users about security risks and best practices.
- Risk Management: Identify, assess, and manage potential security vulnerabilities.
- Incident Response Plans: Procedures for responding to and mitigating security breaches.
3. Physical Measures:
- Access Control: Restrict physical access to sensitive areas and equipment.
- Secure Perimeter: Protect physical facilities with barriers, surveillance, and security personnel.
- Environmental Controls: Maintain proper temperature, humidity, and power conditions to prevent data loss or damage.
National and International Perspectives
Governments around the world recognize the importance of digital security and have developed various frameworks and regulations to promote and enforce security measures. These include:
- National Cybersecurity Strategies: Comprehensive plans outlining national priorities and objectives for digital security.
- Data Protection Laws: Laws that regulate the collection, use, and disclosure of personal data.
- International Agreements: Cooperation between nations to address cross-border cyber threats.
Conclusion
Digital security is a critical aspect of modern society. Understanding the economics and strategies involved in protecting sensitive information is essential for organizations, individuals, and governments alike. By implementing comprehensive security measures and promoting a culture of awareness and responsibility, we can mitigate the risks associated with the digital age and foster a secure online environment for all.