Digital Security: Defending Against Advanced Threats
In the rapidly evolving digital landscape, protecting our sensitive data and systems from sophisticated threats has become paramount. Advanced threats, such as cyber espionage, ransomware, and targeted attacks, pose formidable challenges to organizations and individuals alike. To combat these threats, a robust digital security strategy is essential.
Understanding Advanced Threats
Cyber Espionage: Adversaries use sophisticated techniques to infiltrate networks and extract confidential information, such as trade secrets, financial data, and intellectual property.
Ransomware: Malicious software encrypts victim’s files and demands payment for their release. Extortion and data loss can have severe financial and operational consequences.
Targeted Attacks: Attacks tailored specifically to exploit vulnerabilities in an organization’s systems or infrastructure. They often involve advanced persistent threats (APTs) that remain undetected for extended periods.
Defending against Advanced Threats
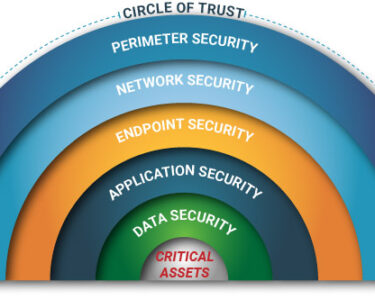
Multi-Layered Defense: Implement a layered approach to security, including firewalls, intrusion detection systems, and endpoint security tools, to protect networks and endpoints from various types of attacks.
Threat Intelligence: Stay informed about emerging threats and vulnerabilities by monitoring threat intelligence sources and sharing information with trusted partners.
Vulnerability Management: Regularly scan systems for vulnerabilities and patch them promptly to prevent exploitation by adversaries.
Access Control: Implement strong access control measures to restrict user access to sensitive data based on the principle of least privilege.
Encryption: Encrypt sensitive data at rest and in transit to protect it from unauthorized access or interception.
Disaster Recovery: Develop and test disaster recovery plans to ensure business continuity in the event of a security breach.
Cybersecurity Awareness Training: Educate employees about cybersecurity risks and best practices to reduce the risk of human error.
Additional Considerations
Zero Trust Architecture: Adopt a zero trust approach, assuming that no user or device within or outside the network is inherently trustworthy.
Incident Response Plan: Have a clear incident response plan in place to effectively contain and mitigate security breaches.
Threat Hunting: Actively search for and address potential threats within the network using advanced security analytics and threat hunting techniques.
Conclusion
Defending against advanced threats requires a comprehensive approach that addresses vulnerabilities, monitors threats, and implements robust security measures. By embracing multi-layered defenses, leveraging threat intelligence, and empowering employees with cybersecurity awareness, organizations can significantly enhance their digital security posture and protect their critical assets from sophisticated threats. Remember, digital security is an ongoing journey that requires constant vigilance and adaptation to stay ahead of the evolving threat landscape.