Digital Security: Combatting Ransomware Threats
In a rapidly evolving digital landscape, ransomware attacks have emerged as a significant threat, posing severe risks to businesses and individuals alike. Ransomware is a type of malicious software that encrypts files and demands payment in exchange for decrypting them. The consequences of such attacks can be devastating, leading to data loss, financial losses, and reputational damage.
Understanding Ransomware
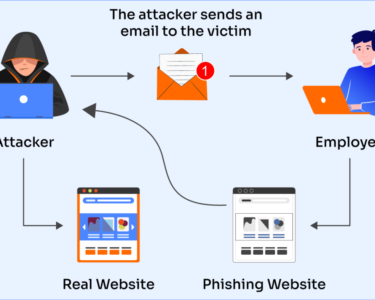
Ransomware typically spreads through phishing emails, malicious websites, or software vulnerabilities. Once installed on a victim’s device, it scans the system for files to encrypt. The infected files become inaccessible, and the user receives a ransom note demanding payment in cryptocurrency (such as Bitcoin) to regain access.
Impact of Ransomware
The impact of ransomware attacks can be multifaceted:
- Data Loss: Ransomware can render valuable files worthless, causing significant data loss.
- Financial Losses: Victims often face substantial financial losses to pay the ransom or recover from the attack.
- Business Interruption: Ransomware can disrupt business operations by freezing access to key files, leading to downtime and productivity loss.
- Reputational Damage: Ransomware attacks can undermine a company’s reputation, erode customer trust, and deter future business.
Combatting Ransomware
To combat ransomware threats effectively, businesses and individuals should implement a comprehensive cybersecurity strategy that includes:
1. Education and Awareness:
- Train employees on ransomware identification and avoidance techniques.
- Conduct regular cybersecurity awareness campaigns to promote best practices.
2. Strong Antivirus and Security Measures:
- Utilize robust antivirus software that can detect and remove known ransomware strains.
- Implement firewalls and intrusion detection systems to block malicious traffic.
- Keep software and operating systems up-to-date with security patches.
3. Data Backup and Recovery:
- Regularly back up critical data to a secure location offline or in the cloud.
- Test backups to ensure they are complete and accessible.
4. Incident Response Plan:
- Develop a comprehensive incident response plan that outlines steps to take in the event of a ransomware attack.
- This should include isolating infected devices, contacting law enforcement, and engaging cybersecurity professionals.
5. Threat Intelligence and Monitoring:
- Subscribe to threat intelligence feeds and monitor cybersecurity forums for information on emerging ransomware threats.
- Use security monitoring tools to detect suspicious activities and respond promptly to potential attacks.
6. Multi-factor Authentication:
- Implement multi-factor authentication to add an extra layer of security to accounts and prevent unauthorized access.
Conclusion
Ransomware threats are a serious concern in the digital age, posing risks to businesses and individuals alike. By implementing a comprehensive cybersecurity strategy that includes education, strong security measures, data backup and recovery, incident response plans, threat intelligence, and multi-factor authentication, it is possible to combat ransomware and mitigate its potential impact. Regular vigilance and ongoing cybersecurity best practices are essential for maintaining a secure digital environment.