MFA Bypass: Attackers Hone Techniques to Evade Multi-Factor Authentication
Introduction
Multi-factor authentication (MFA) has emerged as a crucial defense against cyberattacks by enhancing authentication processes with additional layers of security. However, attackers are persistently innovating methods to bypass MFA, undermining its intended effectiveness.
Vulnerabilities Exploited in MFA Bypass
Attackers leverage various vulnerabilities inherent in MFA implementations to bypass these protections:
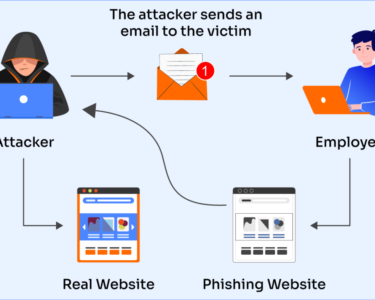
- Phishing: Phishing campaigns target users to obtain their credentials and passcodes, granting attackers access to authenticated accounts without additional verification.
- Man-in-the-Middle (MitM) Attacks: Interception of network traffic allows attackers to steal tokens, session cookies, and other authentication data during MFA authentication.
- SIM Swapping: Attackers fraudulently transfer victims’ phone numbers to their own devices, enabling them to receive MFA codes and bypass authentication controls.
- Malware: Malicious software installed on victims’ devices can intercept MFA prompts and provide attackers with the required authentication factors.
Consequences of MFA Bypass
Successful MFA bypass has dire consequences for organizations and individuals:
- Data Breaches: Access to authenticated accounts enables attackers to steal sensitive data, including financial information, personal data, and confidential business documents.
- Account Takeovers: Attackers can seize control of compromised accounts, impersonating users to commit fraud, steal funds, or disrupt operations.
- Reputational Damage: MFA breaches erode trust in organizations and their security measures, damaging their reputation and customer loyalty.
Mitigating MFA Vulnerabilities
To address MFA vulnerabilities and strengthen multi-factor authentication, organizations should consider the following measures:
- Educate Users: Train users to recognize and avoid phishing attacks, MitM threats, and other social engineering techniques.
- Enhance Token Security: Implement strong mechanisms to protect MFA tokens, such as hardware-based tokens, OTP generators, and biometrics.
- Implement Context-Aware Access: Use contextual information, such as user location, device type, and transaction pattern analysis, to detect and block anomalous authentication attempts.
- Monitor and Detect Suspicious Activity: Regularly review authentication logs, analyze user behavior, and set up alerts to identify potential MFA bypass attempts.
Conclusion
MFA bypass remains a significant challenge, as attackers continuously evolve their techniques. By understanding MFA vulnerabilities, implementing robust mitigation measures, and educating users, organizations can strengthen their authentication mechanisms and protect against this growing cybersecurity threat.