Emerging Threats in Digital Security: Navigating the Evolving Landscape
The digital realm has become an integral part of our modern lives, connecting us, facilitating communication, and powering countless industries. However, as our reliance on technology grows, so too does the threat of cyberattacks. Emerging threats in digital security pose significant challenges, requiring constant vigilance and proactive measures.
1. Ransomware Evolution:
Ransomware remains a prevalent threat, with attackers targeting businesses and individuals alike. The sophistication of ransomware has evolved, making attacks more difficult to detect and mitigate. Ransomware-as-a-service (RaaS) models have enabled even less skilled criminals to launch devastating attacks.
2. Supply Chain Attacks:
The interconnected nature of global supply chains has created new attack vectors. Attackers can compromise software or hardware products during their development or distribution, enabling them to gain access to multiple organizations and sensitive data.
3. Cloud Security Breaches:
Cloud computing has become increasingly popular, but it also introduces security risks. Mishandled cloud configurations or vulnerabilities in cloud services can give attackers a foothold to access data and compromise systems.
4. Internet of Things (IoT) Vulnerabilities:
The proliferation of IoT devices has expanded the attack surface. These devices often lack adequate security measures, making them easy targets for attackers to gain entry to networks and pilfer data.
5. Artificial Intelligence (AI) Threats:
AI can be used both for malicious and beneficial purposes. Attackers can leverage AI to automate attacks, evade detection, and create sophisticated phishing campaigns.
Mitigating Emerging Threats:
Addressing these emerging threats requires a multi-layered approach:
- Strong Authentication: Implement multi-factor authentication and enforce strong passwords to prevent unauthorized access.
- Network Segmentation: Divide networks into logical segments to limit the impact of breaches and isolate critical assets.
- Patch Management: Regularly update software and firmware to patch vulnerabilities and prevent attackers from exploiting them.
- Cloud Security Best Practices: Follow industry guidelines and implement robust security measures for cloud environments.
- IoT Security: Enforce security protocols, use secure gateways, and limit IoT device connectivity to essential services.
- AI Threat Monitoring: Monitor AI systems for suspicious activity and develop countermeasures to mitigate potential threats.
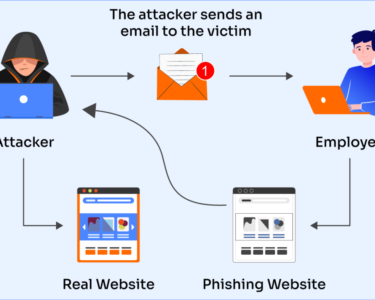
- Educate Users: Train employees and users on cybersecurity best practices, such as spotting phishing emails and reporting suspicious activity.
Conclusion:
Emerging threats in digital security pose constant challenges that require proactive measures. By understanding these threats and implementing robust mitigation strategies, organizations and individuals can protect their data, systems, and assets. Staying informed about the latest threats and adopting a comprehensive cybersecurity strategy is essential to navigating the evolving digital landscape safely and securely.