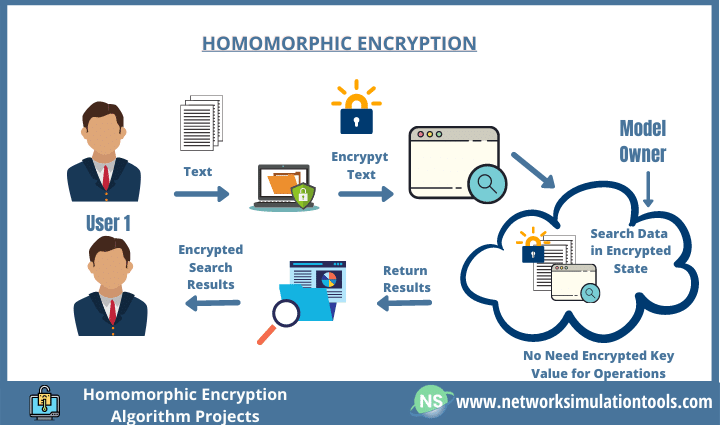
Homomorphic Encryption – This encryption allows for data to be processed without being decrypted, which is important for privacy-preserving data analysis.
Homomorphic Encryption: Empowering Data Analysis While Preserving Privacy Introduction Data analysis has become an indispensable aspect of modern society, aiding us in understanding complex patterns, making informed decisions, and driving innovation. However, traditional data analysis methods often require data to be decrypted before processing, which poses privacy concerns when dealing with sensitive or confidential information. […]
Read More