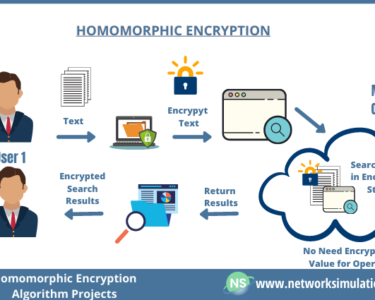
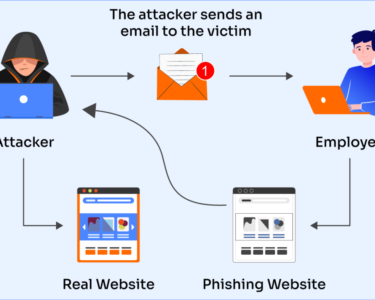
Cyber Threats in the Digital Age
In the contemporary era, where technology permeates every aspect of our lives, the digital realm has become an integral part of our existence. However, this interconnectedness has also ushered in a new era of cyber threats, posing significant risks to individuals, organizations, and nations alike.
Types of Cyber Threats
The landscape of cyber threats is vast and constantly evolving. Some of the most prevalent types include:
- Malware: Malicious software designed to damage or steal data from devices, such as viruses, worms, ransomware, and spyware.
- Phishing: Scams that attempt to trick users into revealing sensitive information, such as passwords or credit card numbers.
- Hacking: Unauthorized access to computer systems or networks to gain access to sensitive data or disrupt operations.
- Social engineering: Techniques used to manipulate individuals into providing sensitive information or taking actions that compromise their security.
- Data breaches: Theft or loss of sensitive personal or corporate data due to security vulnerabilities or malicious attacks.
Impacts of Cyber Threats
The consequences of cyber attacks can be far-reaching and devastating. They can:
- Financial Losses: Data breaches and ransomware attacks can result in significant financial losses for individuals and organizations.
- Reputation Damage: Compromised data or disrupted operations can damage the reputation of businesses and government agencies.
- National Security Risks: Cyber attacks on critical infrastructure, such as power grids or financial systems, can have serious national security implications.
- Privacy Violations: Data breaches can expose sensitive personal information, leading to identity theft, fraud, and other forms of digital harassment.
Mitigating Cyber Threats
Defending against cyber threats requires a multi-layered approach involving:
- Strong Security Measures: Implement robust security measures, such as firewalls, anti-malware software, and secure passwords.
- Educating Users: Train employees and the general public about cyber threats and how to protect themselves.
- Cyber Security Incident Response Plans: Establish clear plans for responding to and recovering from cyber attacks.
- Collaboration and Information Sharing: Foster collaboration between governments, law enforcement agencies, and the private sector to share intelligence and coordinate efforts.
- Investment in Cyber Security Research and Development: Support research and development efforts to improve cyber security technologies and stay ahead of emerging threats.
Conclusion
Cyber threats are an intrinsic part of the digital age. By understanding these threats and implementing comprehensive mitigation strategies, individuals, organizations, and nations can protect themselves from their devastating consequences. It is essential for everyone to remain vigilant, adapt to evolving threat landscapes, and work together to create a safer and more secure digital environment.