Demystifying Digital Defense: A Guide to Protecting Your Online Assets
In the digital age, we rely heavily on technology for communication, work, and entertainment. However, this increased connectivity has also brought with it a surge in cyber threats. To protect your online assets, it’s crucial to understand the basics of digital defense.
What is Digital Defense?
Digital defense refers to the strategies and measures taken to safeguard your online data, systems, and devices from unauthorized access, damage, or theft. It encompasses a wide range of activities, including:
- Firewalls: Software or hardware systems that block unauthorized traffic from entering or leaving a network.
- Antivirus and Antimalware: Programs that detect, quarantine, and remove malicious software from computers and devices.
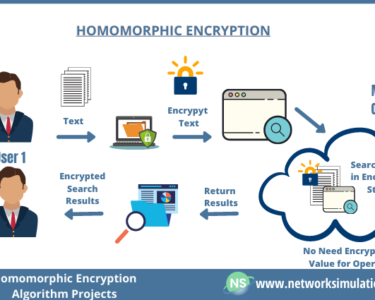
- Data encryption: Converting data into a format that makes it unreadable to unauthorized parties.
- Access control: Restricting who has access to sensitive data and systems.
- Security monitoring: Regularly checking for suspicious activity and potential threats.
Why is Digital Defense Important?
Digital defense is essential for several reasons:
- Protecting personal information: Cybercriminals can use stolen personal data for identity theft, financial fraud, or other malicious purposes.
- Safeguarding business assets: Losing sensitive business data can damage reputation, disrupt operations, and lead to financial losses.
- Preventing data breaches: Cyberattacks can result in the theft or exposure of sensitive data, which can have severe consequences for individuals and organizations.
- Mitigating financial loss: Cybercrime can lead to direct financial losses through theft, extortion, or business disruption.
Best Practices for Digital Defense
To effectively protect your digital assets, follow these best practices:
- Use strong passwords: Create unique and complex passwords for all your online accounts.
- Enable two-factor authentication (2FA): Add an extra layer of security by requiring a second authentication method, such as a text message or email code.
- Update software regularly: Install security updates and patches as soon as they become available.
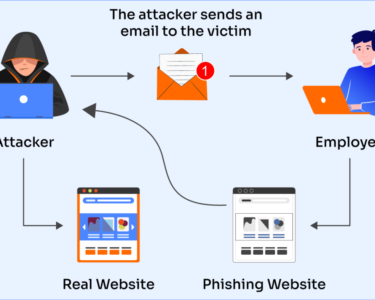
- Be cautious about clicking links and attachments: Avoid clicking on suspicious links or attachments, especially in emails from unknown senders.
- Use a reputable VPN: A virtual private network (VPN) encrypts your internet traffic, protecting your data from eavesdropping.
- Back up your data regularly: Keep multiple copies of important data in secure locations, such as external hard drives or cloud storage.
- Educate yourself and your staff: Stay informed about the latest cyber threats and best practices for digital defense.
Conclusion
Digital defense is a continuous process that requires ongoing attention and effort. By implementing the strategies and best practices outlined in this guide, you can significantly reduce the risk of cyberattacks and protect your online assets. Remember, the key to effective digital defense is to be proactive, vigilant, and constantly adapt to the evolving threatscape.