Digital Security for the Tech-Savvy Generation
In a world where technology pervades every aspect of our lives, digital security has become paramount. As the tech-savvy generation, we possess an unprecedented level of access to information and connectivity, but this comes with inherent risks. To navigate the digital realm safely, it is imperative that we adopt a proactive approach to digital security.
Understanding the Threats
Cyber threats are constantly evolving, making it essential to stay informed about the latest risks. Some common threats include:
- Malware: Malicious software that can damage your devices or steal your data.
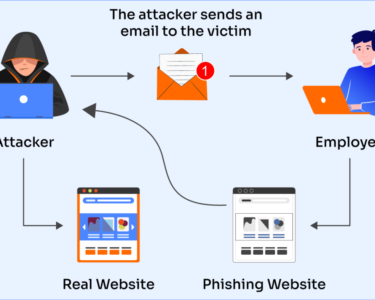
- Phishing: Scams that attempt to trick you into revealing sensitive information.
- Identity theft: The unauthorized use of your personal information to commit fraud.
- Ransomware: Software that encrypts your files and demands a ransom for their release.
- DDoS attacks: Overwhelming a website or server with traffic to make it inaccessible.
Best Practices for Digital Security
- Use strong passwords: Create complex passwords that include a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like your name or birthdate.
- Enable two-factor authentication (2FA): Add an extra layer of security by requiring a second form of verification, such as a code sent to your phone, when logging into accounts.
- Be cautious with email attachments: Never open attachments from unknown senders or suspicious websites.
- Update software regularly: Software updates often include security patches that fix vulnerabilities. Make sure to update your operating systems, apps, and web browsers as soon as possible.
- Use a VPN: A virtual private network (VPN) encrypts your internet traffic, making it more difficult for hackers to intercept your data.
- Use antivirus and antimalware software: Install reputable antivirus and antimalware programs on all your devices to detect and remove threats.
- Monitor your credit reports: Regularly check your credit reports for any suspicious activity that could indicate identity theft.
- Be aware of social engineering: Scammers often use social engineering techniques, such as phishing or pretexting, to trick you into giving up your personal information.
- Back up your data: Regularly back up your important files to a secure location in case your devices are compromised.
Cyber Hygiene
Beyond technical measures, it is equally important to practice good cyber hygiene:
- Be mindful of what you share online: Avoid posting sensitive information on social media or public forums.
- Be aware of privacy settings: Understand the privacy settings on your social media accounts and apps and adjust them accordingly.
- Use different passwords for different accounts: This will reduce the risk of one compromised password granting access to all your accounts.
- Be cautious of public Wi-Fi: When using public Wi-Fi networks, be aware that your data may be less secure. Avoid accessing sensitive information or making online purchases on these networks.
The Role of Education
Education is key to fostering a culture of digital security. Schools, universities, and organizations should provide training on best practices for protecting against cyber threats. By raising awareness and equipping individuals with the knowledge and skills they need, we can empower them to navigate the digital realm safely.
Conclusion
Digital security is a shared responsibility that requires vigilance and ongoing effort from all of us. By adopting best practices, practicing cyber hygiene, and staying informed about evolving threats, the tech-savvy generation can mitigate risks and harness the full potential of the digital age without compromising our privacy or safety. Remember, digital security is not just about protecting devices; it is about safeguarding our identities, information, and overall well-being in the increasingly interconnected world we live in.