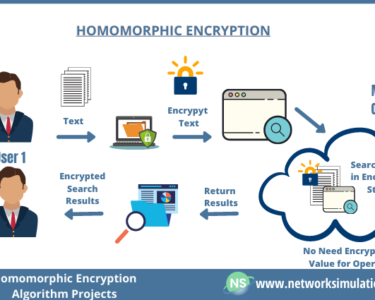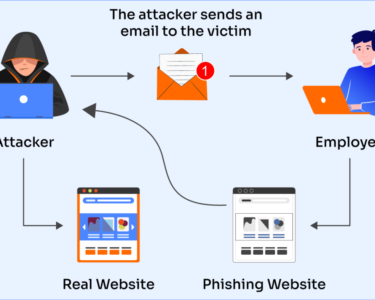
Digital Security: Incident Response Best Practices
In the digital age, data breaches and cyberattacks are becoming increasingly common. Having a robust incident response plan in place is crucial for organizations to mitigate the impact of these events and protect their sensitive data. Here are some best practices for developing an effective incident response plan:
1. Establish a Clear Incident Response Team:
Identify a cross-functional team of experts from IT, security, legal, and business units to manage incident response efforts. Define roles and responsibilities clearly.
2. Develop a Comprehensive Incident Response Plan:
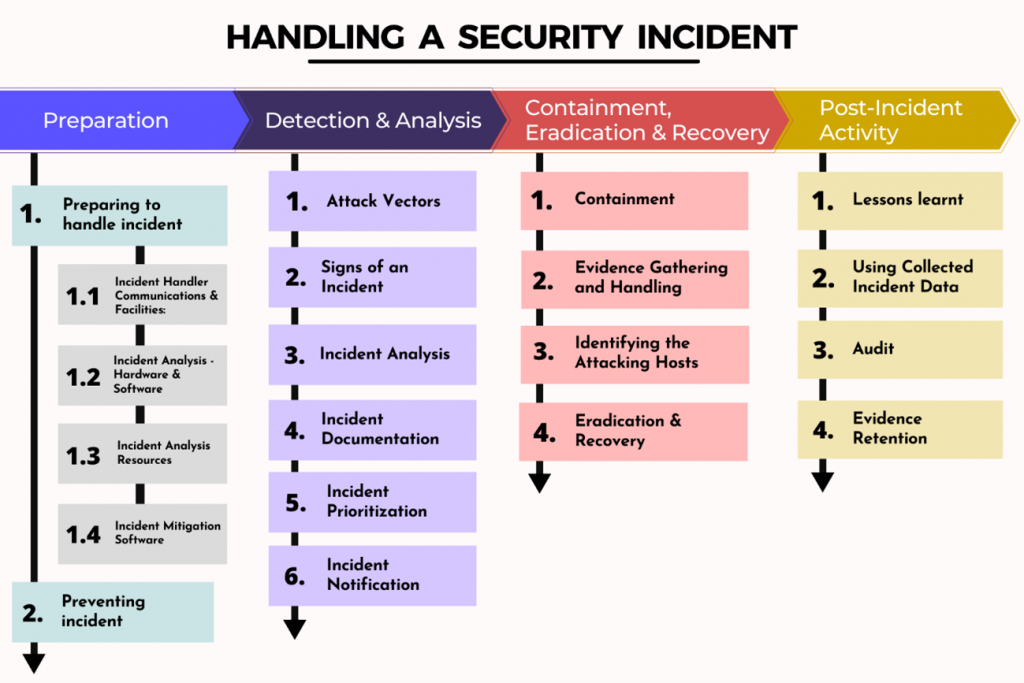
Document detailed procedures outlining the steps to be taken when an incident occurs, including:
- Incident detection and reporting
- Containment and isolation
- Investigation and analysis
- Remediation and recovery
- Communication and reporting
3. Utilize Incident Response Tools:
Invest in tools that automate incident detection, triage, and response. These tools can speed up the response process and enhance visibility.
4. Conduct Regular Training and Exercises:
Train the incident response team and other key personnel on the incident response plan. Conduct periodic exercises to test the plan’s effectiveness and identify areas for improvement.
5. Establish a Communication Plan:
Develop a clear communication strategy to ensure timely and accurate information sharing during an incident. Identify key stakeholders and define their communication channels.
6. Preserve Evidence:
Secure and preserve all relevant evidence, such as system logs, network traffic, and compromised files. This will aid in forensic analysis and legal proceedings.
7. Engage Legal Counsel Early:
Involve legal counsel early in the incident response process to provide guidance on legal compliance, data privacy, and breach notification requirements.
8. Document the Incident Response:
Maintain detailed documentation of all actions taken during the incident response. This will facilitate review, lessons learned, and compliance audits.
9. Perform Post-Incident Analysis:
Once the incident is resolved, conduct a thorough post-incident analysis to identify root causes, evaluate the effectiveness of the response plan, and make necessary improvements.
10. Continuous Improvement:
Incident response plans should be regularly reviewed and updated to reflect changes in technology, threats, and organizational needs.
Conclusion:
Implementing these incident response best practices will help organizations prepare for and respond effectively to data breaches and cyberattacks. A well-coordinated and documented incident response plan will minimize damage, protect sensitive data, and maintain business continuity in the face of cybersecurity threats. By embracing these best practices, organizations can enhance their digital security posture and safeguard their critical assets.