Protecting Digital Assets from Cyber Espionage
In the digital age, businesses and organizations rely heavily on their digital assets, including sensitive data, intellectual property, and financial information. These assets are increasingly under threat from cyber espionage, a form of cybercrime that involves unauthorized access and theft of valuable information by malicious actors.
Cyber espionage poses significant risks to businesses, including:
- Financial losses: Stolen data can be used for fraud, extortion, or insider trading, leading to financial losses.
- Intellectual property theft: Cyber espionage can result in the theft of valuable trade secrets, research data, or product designs, giving competitors an unfair advantage.
- Reputational damage: Data breaches can damage a company’s reputation and erode customer trust.
- National security threats: Cyber espionage can compromise national security if stolen data includes classified information or infrastructure vulnerabilities.
Protecting Against Cyber Espionage
To protect digital assets from cyber espionage, businesses and organizations should implement a comprehensive cybersecurity strategy that includes the following measures:
1. Strong Access Controls:
- Implement multi-factor authentication for user access.
- Enforce strong password policies and regularly update passwords.
- Limit user access to sensitive data on a need-to-know basis.
2. Network Security:
- Use firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to monitor and protect network traffic.
- Patch and update software regularly to address vulnerabilities.
- Monitor network activity for suspicious behavior or anomalies.
3. Data Protection:
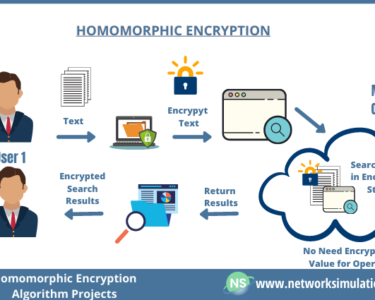
- Encrypt sensitive data at rest and in transit.
- Use data loss prevention (DLP) solutions to prevent data exfiltration.
- Implement data backups and recovery plans to minimize data loss risks.
4. Employee Training:
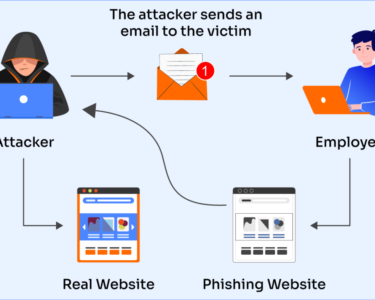
- Educate employees on cybersecurity best practices, including phishing awareness and social engineering techniques.
- Train employees on handling and safeguarding sensitive data.
- Foster a culture of cybersecurity awareness and vigilance.
5. Vulnerability Management:
- Regularly scan for vulnerabilities in systems, networks, and applications.
- Prioritize and patch vulnerabilities based on their severity and impact.
- Conduct penetration testing to assess the effectiveness of security controls.
6. Threat Intelligence:
- Monitor cybersecurity news and alerts to stay informed about emerging threats.
- Share threat intelligence with industry peers and law enforcement.
- Use threat intelligence tools to identify and mitigate potential attacks.
7. Incident Response:
- Develop a comprehensive incident response plan to guide actions during a cyber attack.
- Conduct regular incident response exercises to test and improve response capabilities.
- Notify appropriate authorities and stakeholders in case of a data breach.
Conclusion
Protecting digital assets from cyber espionage is crucial for businesses and organizations to safeguard their sensitive information, avoid financial losses, and maintain their reputation. By implementing a comprehensive cybersecurity strategy that covers access controls, network security, data protection, employee training, vulnerability management, threat intelligence, and incident response, organizations can mitigate the risks of cyber espionage and protect their valuable digital assets.