Securing Critical Infrastructure Digitally
Critical infrastructure, such as power plants, water treatment facilities, and transportation networks, is essential for the functioning of modern society. However, with the increasing reliance on digital technologies, these systems are becoming increasingly vulnerable to cyberattacks.
Threats to Critical Infrastructure
There are various threats to critical infrastructure in the digital age:
- Malware: Malicious software, such as ransomware, can disrupt operations and cause significant damage.
- DDoS attacks: Distributed Denial of Service (DDoS) attacks can overwhelm networks and make systems inaccessible.
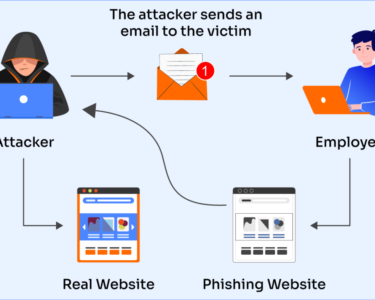
- Phishing and social engineering: Cybercriminals use phishing emails and social engineering techniques to trick employees into providing sensitive information or access to systems.
- Insider threats: Employees with malicious intent or limited cybersecurity awareness can compromise systems and cause damage.
Cybersecurity Measures for Critical Infrastructure
To mitigate these threats, it is crucial to implement robust cybersecurity measures for critical infrastructure:
- Network Segmentation: Segmenting networks into smaller zones reduces the potential impact of an attack by isolating infected devices.
- Multi-Factor Authentication: Implementing multi-factor authentication requires users to provide multiple forms of identification, making it more difficult for attackers to gain access.
- Intrusion Detection and Prevention Systems (IDS/IPS): IDS/IPS monitor network traffic for suspicious activity and take action to block attacks.
- Security Monitoring and Incident Response: Continuously monitoring systems for potential threats and having a plan in place for incident response is essential for timely mitigation of attacks.
- Employee Training and Awareness: Educating employees about cybersecurity best practices and social engineering tactics is crucial to prevent them from becoming victims of attacks.
Government and Industry Collaboration
Securing critical infrastructure requires collaboration between governments, utilities, and technology providers. Governments can establish regulations and standards, provide funding for cybersecurity initiatives, and coordinate incident response efforts. Utilities must invest in robust cybersecurity measures and work with technology providers to develop and implement innovative solutions.
Conclusion
Securing critical infrastructure digitally is vital for the continuity and safety of modern society. By implementing robust cybersecurity measures, educating employees, and fostering collaboration, we can mitigate the threats and ensure the resilience of these essential systems. It is an ongoing effort that requires constant vigilance and adaptation to the evolving threat landscape.