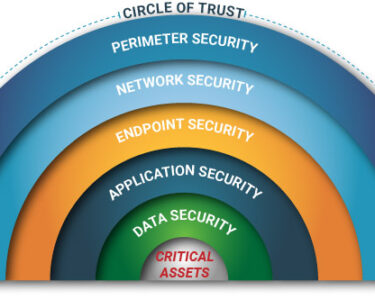
Digital Security: Embracing Threat Intelligence
In the ever-evolving landscape of digital security, organizations face an increasing number of sophisticated cyber threats. To effectively combat these threats, it is crucial for organizations to embrace threat intelligence as a cornerstone of their security strategy.
What is Threat Intelligence?
Threat intelligence is the continuous and systematic collection, analysis, and interpretation of data about potential and existing threats to an organization. It involves gathering information from various sources, including:
- Cybercrime forums
- Security blogs
- Threat feeds
- Honeypots
- Intrusion detection systems
Benefits of Threat Intelligence
By leveraging threat intelligence, organizations can:
- Identify emerging threats: Detect new vulnerabilities and attack methods before they can be exploited.
- Prioritize security efforts: Allocate resources to the most critical threats based on their potential impact.
- Improve threat detection and response: Use threat intelligence to enhance the effectiveness of security tools and incident response procedures.
- Inform security decision-making: Provide actionable insights to guide security investments and policies.
- Collaborate with external stakeholders: Share threat intelligence with industry partners to enhance collective security.
Components of a Threat Intelligence Program
To successfully implement a threat intelligence program, organizations should consider the following components:
- Data Collection: Establish a comprehensive data gathering process to acquire threat-related information from various sources.
- Analysis: Analyze collected data to identify patterns, trends, and potential threats.
- Interpretation: Determine the significance of threats based on their potential impact and likelihood of occurrence.
- Dissemination: Distribute threat intelligence to relevant stakeholders within the organization, including security teams and business leaders.
- Feedback: Continuously evaluate the effectiveness of the threat intelligence program and incorporate feedback to improve its accuracy and relevance.
Types of Threat Intelligence
There are various types of threat intelligence, each serving a specific purpose:
- Strategic intelligence: Provides long-term insights into the broader threat landscape and emerging trends.
- Tactical intelligence: Focuses on immediate and actionable threats that can impact the organization’s operations.
- Technical intelligence: Provides detailed information about specific vulnerabilities, exploits, and attack techniques.
Conclusion
Threat intelligence is an indispensable asset for organizations seeking to enhance their digital security. By embracing threat intelligence, organizations can proactively identify and respond to emerging threats, prioritize security investments, and effectively manage the risks associated with the increasingly complex cyber threat landscape. By investing in a robust threat intelligence program, organizations can protect their critical assets, reputation, and overall business operations.